Info about back track , penetration testing and metasploit framework.
Friday, October 5, 2012
Monday, June 15, 2009
A Brief Virus knowledge..u need to know
A virus is a computer program file capable of attaching to disks or other files and replicating itself repeatedly, typically without user knowledge or permission. Some viruses attach to files so when the infected file executes, the virus also executes. Other viruses sit in a computer's memory and infect files as the computer opens, modifies, or creates the files. Some viruses display symptoms, and others damage files and computer systems, but neither is essential in the definition of a virus; a non-damaging virus is still a virus.......Lipak
Below are some description of virus terminology u need to know.....this is what from my experience and reference.........Lipak
Variant
A variant is a modified version of a virus. It is usually produced on purpose by the virus author or another person amending the virus code. If changes to the original are small, most anti-virus products will also detect variants. However, if the changes are large, the variant may go undetected by anti-virus software
Signature
A signature is a search pattern—often a simple string of characters or bytes—expected to be found in every instance of a particular virus. Usually, different viruses have different signatures. Anti-virus scanners use signatures to locate specific viruses.
Payload
Payload refers to the effects produced by a virus attack. It sometimes refers to a virus associated with a dropper or Trojan horse
On-access scanner
An on-access scanner is a real-time virus scanner that scans disks and files automatically in the background as the computer accesses the files.
Stealth virus
Stealth viruses attempt to conceal their presence from anti-virus software. Many stealth viruses intercept disk-access requests, so when an anti-virus application tries to read files or boot sectors to find the virus, the virus feeds the program a "clean" image of the requested item. Other viruses hide the actual size of an infected file and display the size of the file before infection.
Self-garbling Viruses
A self-garbling virus attempts to hide from anti-virus software by garbling its own code. When these viruses spread, they change the way they are encoded so anti-virus software cannot find them. A small portion of the virus code decodes the garbled code when activated
Self-encrypting virus
Self-encrypting viruses attempt to conceal themselves from anti-virus programs. Most anti-virus programs attempt to find viruses by looking for certain patterns of code (known as virus signatures) that are unique to each virus. Self-encrypting viruses encrypt these text strings differently with each infection to avoid detection.
Resident extension
A resident extension is a memory-resident portion of a program that remains active after the program ends. It essentially becomes an extension to the operating system. Many viruses install themselves as resident extensions.
Resident virus
A resident virus loads into memory and remains inactive until a trigger event. When the event occurs, the virus activates, either infecting a file or disk, or causing other consequences. All boot viruses are resident viruses and so are the most common file viruses.
Replication
Replication is the process by which a virus makes copies of itself in order to carry out subsequent infections. Replication is one of major criteria separating viruses from other computer programs
Polymorphic virus
Polymorphic viruses create varied (though fully functional) copies of themselves as a way to avoid detection by anti-virus software. Some polymorphic virus use different encryption schemes and require different decryption routines. Thus, the same virus may look completely different on different systems or even within different files. Other polymorphic viruses vary instruction sequences and use false commands in the attempt to thwart anti-virus software. One of the most advanced polymorphic viruses uses a mutation engine and random-number generators to change the virus code and its decryption routine
Overwriting virus
An overwriting virus copies its code over its host file's data, thus destroying the original program. Disinfection is possible, although files cannot be recovered. It is usually necessary to delete the original file and replace it with a clean copy.
Multipartite virus
Multipartite viruses use a combination of techniques including infecting documents, executables and boot sectors to infect computers. Most multipartite viruses first become resident in memory and then infect the boot sector of the hard drive. Once in memory, multipartite viruses may infect the entire system.
Removing multipartite viruses requires cleaning both the boot sectors and any infected files. Before you attempt the repair, you must have a clean, write-protected rescue disk.
Mutating virus
A mutating virus changes, or mutates, as it progresses through its host files making disinfection more difficult. The term usually refers to viruses that intentionally mutate, though some experts also include non-intentionally mutating viruses. Also see: polymorphic virus.
Memory-resident virus
A memory-resident virus stays in memory after it executes, and it infects other files when certain conditions are met. In contrast, non-memory-resident viruses are active only while an infected application runs.
Macro virus
A macro virus is a malicious macro. Macro viruses are written in a macro programming language and attach to a document file such as Word or Excel. When a document or template containing the macro virus is opened in the target application, the virus runs, does its damage, and copies itself into other documents. Continual use of the program results in the spread of the virus.
False negative
A false negative error occurs when anti-virus software fails to indicate that an infected file is truly infected. False negatives are more serious than false positives, although both are undesirable. False negatives are more common with anti-virus software because the may miss a new or a heavily modified virus. Also see: false positive.
False positive
A false positive error occurs when anti-virus software wrongly claims that a virus is infecting a clean file. False positives usually occur when the string chosen for a given virus signature is also present in another program. Also see: false negative.
Dropper
A dropper is a carrier file that installs a virus on a computer system. Virus authors often use droppers to shield their viruses from anti-virus software. The term injector often refers to a dropper that installs a virus only in memory.
Direct action virus
A direct-action virus works immediately to load itself into memory, infect other files, and then to unload itself.
Companion virus
Companion viruses use a feature of DOS that allows software programs with the same name, but with different extensions, to operate with different priorities. Most companion viruses create a COM file which has a higher priority than an EXE file with the same name.
COM file
A COM file is a type of executable file limited to 64 kb. These simple files are often used for utility programs and small routines. Because COM files are executable, viruses can infect them. This file type has the extension COM.
Thus, a virus may see a system contains the file PROGRAM.EXE and create a file called PROGRAM.COM. When the computer executes PROGRAM from the command line, the virus (PROGRAM.COM) runs before the actual PROGRAM.EXE. Often the virus will execute the original program afterwards so the system appears normal.
Cluster virus
Cluster viruses modify the directory table entries so the virus starts before any other program. The virus code only exists in one location, but running any program runs the virus as well. Because they modify the directory, cluster viruses may appear to infect every program on a disk. They are also called file system viruses.
Cavity virus
A cavity virus overwrites a part of its host file without increasing the length of the file while also preserving the host's functionality.
Lipak
email : lipaknitjsr@ethicalhackers.net
Below are some description of virus terminology u need to know.....this is what from my experience and reference.........Lipak
Variant
A variant is a modified version of a virus. It is usually produced on purpose by the virus author or another person amending the virus code. If changes to the original are small, most anti-virus products will also detect variants. However, if the changes are large, the variant may go undetected by anti-virus software
Signature
A signature is a search pattern—often a simple string of characters or bytes—expected to be found in every instance of a particular virus. Usually, different viruses have different signatures. Anti-virus scanners use signatures to locate specific viruses.
Payload
Payload refers to the effects produced by a virus attack. It sometimes refers to a virus associated with a dropper or Trojan horse
On-access scanner
An on-access scanner is a real-time virus scanner that scans disks and files automatically in the background as the computer accesses the files.
Stealth virus
Stealth viruses attempt to conceal their presence from anti-virus software. Many stealth viruses intercept disk-access requests, so when an anti-virus application tries to read files or boot sectors to find the virus, the virus feeds the program a "clean" image of the requested item. Other viruses hide the actual size of an infected file and display the size of the file before infection.
Self-garbling Viruses
A self-garbling virus attempts to hide from anti-virus software by garbling its own code. When these viruses spread, they change the way they are encoded so anti-virus software cannot find them. A small portion of the virus code decodes the garbled code when activated
Self-encrypting virus
Self-encrypting viruses attempt to conceal themselves from anti-virus programs. Most anti-virus programs attempt to find viruses by looking for certain patterns of code (known as virus signatures) that are unique to each virus. Self-encrypting viruses encrypt these text strings differently with each infection to avoid detection.
Resident extension
A resident extension is a memory-resident portion of a program that remains active after the program ends. It essentially becomes an extension to the operating system. Many viruses install themselves as resident extensions.
Resident virus
A resident virus loads into memory and remains inactive until a trigger event. When the event occurs, the virus activates, either infecting a file or disk, or causing other consequences. All boot viruses are resident viruses and so are the most common file viruses.
Replication
Replication is the process by which a virus makes copies of itself in order to carry out subsequent infections. Replication is one of major criteria separating viruses from other computer programs
Polymorphic virus
Polymorphic viruses create varied (though fully functional) copies of themselves as a way to avoid detection by anti-virus software. Some polymorphic virus use different encryption schemes and require different decryption routines. Thus, the same virus may look completely different on different systems or even within different files. Other polymorphic viruses vary instruction sequences and use false commands in the attempt to thwart anti-virus software. One of the most advanced polymorphic viruses uses a mutation engine and random-number generators to change the virus code and its decryption routine
Overwriting virus
An overwriting virus copies its code over its host file's data, thus destroying the original program. Disinfection is possible, although files cannot be recovered. It is usually necessary to delete the original file and replace it with a clean copy.
Multipartite virus
Multipartite viruses use a combination of techniques including infecting documents, executables and boot sectors to infect computers. Most multipartite viruses first become resident in memory and then infect the boot sector of the hard drive. Once in memory, multipartite viruses may infect the entire system.
Removing multipartite viruses requires cleaning both the boot sectors and any infected files. Before you attempt the repair, you must have a clean, write-protected rescue disk.
Mutating virus
A mutating virus changes, or mutates, as it progresses through its host files making disinfection more difficult. The term usually refers to viruses that intentionally mutate, though some experts also include non-intentionally mutating viruses. Also see: polymorphic virus.
Memory-resident virus
A memory-resident virus stays in memory after it executes, and it infects other files when certain conditions are met. In contrast, non-memory-resident viruses are active only while an infected application runs.
Macro virus
A macro virus is a malicious macro. Macro viruses are written in a macro programming language and attach to a document file such as Word or Excel. When a document or template containing the macro virus is opened in the target application, the virus runs, does its damage, and copies itself into other documents. Continual use of the program results in the spread of the virus.
False negative
A false negative error occurs when anti-virus software fails to indicate that an infected file is truly infected. False negatives are more serious than false positives, although both are undesirable. False negatives are more common with anti-virus software because the may miss a new or a heavily modified virus. Also see: false positive.
False positive
A false positive error occurs when anti-virus software wrongly claims that a virus is infecting a clean file. False positives usually occur when the string chosen for a given virus signature is also present in another program. Also see: false negative.
Dropper
A dropper is a carrier file that installs a virus on a computer system. Virus authors often use droppers to shield their viruses from anti-virus software. The term injector often refers to a dropper that installs a virus only in memory.
Direct action virus
A direct-action virus works immediately to load itself into memory, infect other files, and then to unload itself.
Companion virus
Companion viruses use a feature of DOS that allows software programs with the same name, but with different extensions, to operate with different priorities. Most companion viruses create a COM file which has a higher priority than an EXE file with the same name.
COM file
A COM file is a type of executable file limited to 64 kb. These simple files are often used for utility programs and small routines. Because COM files are executable, viruses can infect them. This file type has the extension COM.
Thus, a virus may see a system contains the file PROGRAM.EXE and create a file called PROGRAM.COM. When the computer executes PROGRAM from the command line, the virus (PROGRAM.COM) runs before the actual PROGRAM.EXE. Often the virus will execute the original program afterwards so the system appears normal.
Cluster virus
Cluster viruses modify the directory table entries so the virus starts before any other program. The virus code only exists in one location, but running any program runs the virus as well. Because they modify the directory, cluster viruses may appear to infect every program on a disk. They are also called file system viruses.
Cavity virus
A cavity virus overwrites a part of its host file without increasing the length of the file while also preserving the host's functionality.
Lipak
email : lipaknitjsr@ethicalhackers.net
Sunday, March 8, 2009
VIRUSES AND SAFELY REMOVAL PROBLEM IN THE PEN DRIVE : HOW TO SOLVE IT
Virus in the removal media ,mostly in the pen drive is a common problem as becoz we use it to transfer data between defferent computers.Mostly good antivirus are able to scan and remove all virus/Trojan/worm from it,but still can't remove some malwares due to many reasons say the virus run in the background or it associates or attach itself to some system files.
Even after formatting also u will find that some malware will still remain as it is in your pen drive...this is really amazing but it is possible as the malicious code attached itself to some system files of the pen drive itself.Those virus codes are specifically named as DNA.
Those u may have to remove manually say delete manually.That's what i am giving some methods how to remove it........Lipak
--------------------
1.Connect your pendrive.
2.Go to START ,RUN,type cmd.
3.Check the drive letter of your pendrive(eg.F:).
4.In the command prompt ,type f: and press enter to go into the pen drive's location.
5 .Once u moved to the required drive Type dir /w/o/a/p press enter to see each and every files of your pen drive.
6.See for the files:(or any other virus)
Explorer.exe
Autorun.inf
autorun.exe
NewFolder.exe
regsvr.exe
astry.au3
reg32.exe
Bha.vbs
Iexplore.vbs
Info.exe
New_Folder.exe
Ravmon.exe
Ravon.exe
MntDrCore.exe
RVHost.exe
or any other folder with extension .exe.
7.If you find any of the above files,run the command "attrib -h -r -s -a *.*" at the command prompt and press enter to change the attributes of those files.
8.Delete each file one by one using del filename (eg.del autorun.inf).
9.Finally,scan your pendrive with a good antivirus(eg.McAfee ,Kaspersky).
Some times u often find that u want do safely removal for the pen drive ,but it will not, giving a message that the generic volume is in use ,so it can't be removed.It may be possibvle that u have manually run some programs or files from it and even after closing that program, it is running in the background i.e in the process which u can easily identify seeing all the procees running in the task manager and end it manually.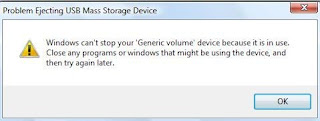
Often this may be due to some virus.In this case u will not be able to identify and end the required process to do safely removal. For this u may use a software Unlocker ( which i use and find it useful) to identiufy the process running from pen drive and u will able to kill it.So u can do safely removal.Finally i will suggest to take atmost care while using pen drive of others or which was attached to some publicly used computer say in cafe or Computer Center (of our collg)............................Lipak
email : lipaknitjsr@gmail.com
Even after formatting also u will find that some malware will still remain as it is in your pen drive...this is really amazing but it is possible as the malicious code attached itself to some system files of the pen drive itself.Those virus codes are specifically named as DNA.
Those u may have to remove manually say delete manually.That's what i am giving some methods how to remove it........Lipak
--------------------
1.Connect your pendrive.
2.Go to START ,RUN,type cmd.
3.Check the drive letter of your pendrive(eg.F:).
4.In the command prompt ,type f: and press enter to go into the pen drive's location.
5 .Once u moved to the required drive Type dir /w/o/a/p press enter to see each and every files of your pen drive.
6.See for the files:(or any other virus)
Explorer.exe
Autorun.inf
autorun.exe
NewFolder.exe
regsvr.exe
astry.au3
reg32.exe
Bha.vbs
Iexplore.vbs
Info.exe
New_Folder.exe
Ravmon.exe
Ravon.exe
MntDrCore.exe
RVHost.exe
or any other folder with extension .exe.
7.If you find any of the above files,run the command "attrib -h -r -s -a *.*" at the command prompt and press enter to change the attributes of those files.
8.Delete each file one by one using del filename (eg.del autorun.inf).
9.Finally,scan your pendrive with a good antivirus(eg.McAfee ,Kaspersky).
Some times u often find that u want do safely removal for the pen drive ,but it will not, giving a message that the generic volume is in use ,so it can't be removed.It may be possibvle that u have manually run some programs or files from it and even after closing that program, it is running in the background i.e in the process which u can easily identify seeing all the procees running in the task manager and end it manually.

Often this may be due to some virus.In this case u will not be able to identify and end the required process to do safely removal. For this u may use a software Unlocker ( which i use and find it useful) to identiufy the process running from pen drive and u will able to kill it.So u can do safely removal.Finally i will suggest to take atmost care while using pen drive of others or which was attached to some publicly used computer say in cafe or Computer Center (of our collg)............................Lipak
email : lipaknitjsr@gmail.com
Friday, January 16, 2009
Why we get less memory space than it mentioned in USB flashdrive/Hard Disk/Memory stick.....
Many of us often think (even i was before) that why we get less memory space in computer world that mentioned .Like in 4 GB pen drive (USB) we get maximun free space 3.73 GB.Am i right ?
Even in HD of 160 GB we get approx 149 GB.Similar case of memory stick and so and so on....
Let me explain clearly the shadow behind it.It is due to conversion of bytes in to Kilo Bytes(KB),
Kilo Bytes in to Mega Bytes(Mb) ,and ofcourse Mega Bytes to Giga Bytes(Gb).Where the factor is of 1024 ,not 1000.
Ok ,let me expalin u clearly this with an example....
Let's take an example of 4 Gb USB pen drive where we at max 3.73 Gb
4 GB = 4 Giga Bytes =4 * (10 ^9) Bytes =4000000000 Bytes (as 1 Giga = 10 ^ 9)
dividing by 1024 = 39,06,250, Kb (as 1 Kb = 1024 Bytes)
dividing again by 1024 = 3814.7 Mb ( as 1 Mb = 1024 Kb)
dividing again by 1024 = 3.73 Gb
So, finally 3.73 Gb is the maximum we can get.
Now, i suppose everybody got my point.........................Lipak
E-mail : lipaknitjsr@gmail.com
Even in HD of 160 GB we get approx 149 GB.Similar case of memory stick and so and so on....
Let me explain clearly the shadow behind it.It is due to conversion of bytes in to Kilo Bytes(KB),
Kilo Bytes in to Mega Bytes(Mb) ,and ofcourse Mega Bytes to Giga Bytes(Gb).Where the factor is of 1024 ,not 1000.
Ok ,let me expalin u clearly this with an example....
Let's take an example of 4 Gb USB pen drive where we at max 3.73 Gb
4 GB = 4 Giga Bytes =4 * (10 ^9) Bytes =4000000000 Bytes (as 1 Giga = 10 ^ 9)
dividing by 1024 = 39,06,250, Kb (as 1 Kb = 1024 Bytes)
dividing again by 1024 = 3814.7 Mb ( as 1 Mb = 1024 Kb)
dividing again by 1024 = 3.73 Gb
So, finally 3.73 Gb is the maximum we can get.
Now, i suppose everybody got my point.........................Lipak
E-mail : lipaknitjsr@gmail.com
Wednesday, January 14, 2009
Troubleshoot Blue Screen Error (Blue Screen Of Death) in Windows OS

One of the most dreaded error messages for a Windows user is
the blue screen, or the Blue Screen of Death (BSOD) as it is popularly
known, which suddenly pops up informing you that
something is seriously wrong with Windows.The “Windows Stop Message”, which is the official name for the BSOD. What this screen essentially means is that Windows has crashed and needs to reboot to recover.
Additionally, the contents of the system memory(physical memory) are dumped to a file(%SystemRoot%\MEMORY.DMP). This memory dump file can be analysed to troubleshoot the problem in depth
All the stop errors are numbered according to the circumstances that caused
the error .Usually, you will be able to recover and continue
without any problems, but it can sometimes be a hair-raising
experience.
The blue screen of death can strike anyone, anywhere. At the Comdex trade show, Microsoft Chairman Bill Gates encountered the blue screen during a demonstration of Windows 98.
The BSOD is the main way for virtual device drivers to report a
problem. The error description will state that Windows faced a
problem (exception) at a particular memory address (a portion of
the RAM) in a certain file, usually with the prefix VxD (virtual
device driver), or the file name may have the DLL extension
Basic cause of blue screen of death-
1.faulty power supply
2.recent hardware or softwarte change
3.device driver problem
4.an overheating processor, a defective memory system, a dying or
dead hard disk, or faulty software and device drivers.
5.memory address conflict in RAM
6.faulty windows installation{hardware or hard disk error during installation} or
7.corrupted or crashed windows due to patch or may be due to malware
The basic approach-
obviously to correct the problem is - first we need to dignose the problem.
we can do it by seeing the list of probable causes or the blue screen error message{by the stop number}
The Stop number will be in hexadecimal format—something like this: STOP : 0x0000000A (0xDB000000, 0x00000001, 0x00000002, 0xB04FB0DB)
Notedown the stop number at first.If u r unable to note it down as windows reboot before it then u can :
clear the automatic boot check box at
rightclick my computer>properties>advanced system setting(vista)/advance(xp)>Advance>startup and recovery setting
Also if u r able to boot into sytem and run it nicely in safe mode{press F8 to do so at boot},then the problem lies
in some software rather than hardware
But If Windows is not
able to boot into Safe Mode, restart the computer, bring up the
Advanced Options screen (by pressing [F8] during POST) and select
“Last Known Good Configuration”. Windows will then attempt to
load the last settings where everything worked normally. If that
doesn’t work, then it most likely means you have a serious hardware
or critical startup system file error. If this error has occurred after
any recent hardware additions, remove the hardware and try to
boot again.
HOW TO SHOOT THE TROUBLE-
If you are able to boot into Safe Mode,
1.first perform a virus and spyware scan using a good antivirus or anti spyware
2.Uninstall any recently added software, and remove or roll back any
updated device drivers{u can do it in device management}
3.u may do System Restore
4.test the RAM for
errors by using a memory diagnostic program such as Windows
Memory Diagnostic
5.If the BSOD is caused by faulty hardware, remove any recently
added hardware—after switching off the PC, of course
6.If the BSOD is due to corrupt system startup files, you can repair
Windows by performing a Repair Install
Common Stop Message error codes and suggested solutions:
1.Stop Code: STOP 0x0000000A
IRQL_NOT_LESS_EQUAL
Code Meaning : Faulty device drivers, or services from backup utilities
or virus scanners
Recommended Resolution: Remove, disable or stop the offending
drivers, backup utilities or anti-virus programs. Get updated software
from the manufacturer.
2.Stop Code: STOP 0x0000001E
KMODE_EXCEPTION_NOT_HANDLED
Code Meaning: Some driver files may be causing a problem.
Recommended Resolution: Remove, disable or update the driverfile
listed in the error message. Verify if new hardware installation
is correct.
3.Stop Code: STOP 0x00000024
NTFS_FILE_SYSTEM
Code Meaning: Usually caused by disk corruption in the NTFS file
system or third-party disk defragmenters.
Recommended Resolution: Use hard disk diagnostic software to
verify that the hard disk is working. Remember to always Use
Microsoft-certified disk defragmenters.
4.Stop Code: STOP 0x0000002E
DATA_BUS_ERROR
Code Meaning: Caused by a parity error in the system memory.
Almost always caused by hardware problems—a configuration
issue, defective hardware, or incompatible hardware.
Recommended Resolution: If physical RAM was recently added to
the system, remove it and see if the error still occurs. If the error
persists, try disabling memory caching in the BIOS. Else remove,
repair or reinstall the defective hardware.
5.Stop Code: STOP 0x00000050
PAGE_FAULT_IN_NONPAGED_AREA
Code Meaning : Caused when requested data is not found in memory;
the system checks the page file, but the missing data is
identified as unable to be written to the page file
Recommended Resolution: Remove any newly-added hardware or
run diagnostic software supplied by the manufacturer to check if
the component has failed. Install updated device drivers or roll
back to a previous driver.
6.Stop Code: STOP 0x0000007B
INACCESSIBLE_BOOT_DEVICE
Code Meaning: Caused when Windows loses access to the system
partition during the Startup process. This can be caused by: an
incorrect driver for a SCSI, RAID, or UDMA IDE controller; incorrect
ARC path in the Boot.ini; or a failed boot device.
Recommended Resolution: Verify that the disk storage device is
installed correctly and working. Reinstall or update the device
driver. Verify that the BIOS setting for the device is correct. Verify
the integrity of the hard disk.
7.Stop Code: STOP 0x0000007F
UNEXPECTED_KERNEL_MODE_TRAP
Code Meaning: Caused when the CPU generates an error that the
kernel does not catch. Usually hardware related—especially RAM.
Can also be caused by CPU overclocking, or defective components
on the motherboard.
Recommended Resolution:
1. Run the memory diagnostic to test RAM.
2. Restore overclocked settings to previous values.
3. Repair/replace the motherboard.
4. Disable sync negotiation in SCSI BIOS; check SCSI termination.
8.Stop Code: STOP 0x000000D1
DRIVER_IRQL_NOT_LESS_OR_EQUAL
Code Meaning: Occurs when the system attempts to access pageable
memory at a process IRQL that is too high
Recommended Resolution: Very similar to STOP 0xA. Remove,
disable or stop the offending drivers, backup utilities or anti-virus
programs. Get updated software from the manufacturer.
9.Stop Code: STOP 0xC000021A
STATUS_SYSTEM_PROCESS_TERMINATED
Code Meaning: Caused when the user-mode subsystem (Winlogon
or CSRSS) is fatally compromised and security cannot be guaranteed.
The most common causes are third-party applications or mismatched
system files.
Recommended Resolution:
1. Remove, disable, or roll back any newly-installed device driver.
2. Uninstall any newly-installed software.
3. Use Windows-compatible backup/restore programs.
4. Restore full control permissions to the local SECURITY account
on the systemroot folder by doing a fresh parallel installation of
Windows on a separate partition.
E-mail: lipaknitjsr@gmail.com
For details about BSOD plz. google it or see how to interprete "MEMORY.DMP" file........Lipak
Saturday, January 10, 2009
BRIEF ABOUT SOME MALICIOUS TOOLS
Spyware
Spyware often gets installed together with “regular” software by irresponsible companies that think they can get away with it. Other spyware is installed by hackers. It collects and transmits information about you for advertising, marketing or even criminal purposes.
Adware
Adware displays advertising. All over the place. Being infested with adware is like having lice in your computer,
it’s annoying all the time and really difficult to get rid of.
Hijackers
These pests hijack your browser, displaying web pages that you don’t want to see and installing annoying “advertising bars” in your browser.
Tracking Cookies
Cookies are generally harmless, but these ones can track everything you do on the net and report it to advertisers or worse.
Hidden Dialers
These evil programs can cost you thousands of dollars by making you access the Internet via a premium-rate number instead of your regular provider.
Worms
The program prevents malicious software from distributing email in your name with viruses and other malware in attachments.
Key Loggers
How do you feel about programs that record and transmit every keystroke you make, with all your personal secrets and credit card details? Not nice? Not nice! So get rid of them!
Trojan Horses
A Trojan Horse or “Trojan” is a hidden program that doesn’t do any damage directly. But it enables hackers to control your computer over the Internet and do practically anything they want – activate your webcam, send spam, attack other computers, use your banking software…all in your name.
Spyware often gets installed together with “regular” software by irresponsible companies that think they can get away with it. Other spyware is installed by hackers. It collects and transmits information about you for advertising, marketing or even criminal purposes.
Adware
Adware displays advertising. All over the place. Being infested with adware is like having lice in your computer,
it’s annoying all the time and really difficult to get rid of.
Hijackers
These pests hijack your browser, displaying web pages that you don’t want to see and installing annoying “advertising bars” in your browser.
Tracking Cookies
Cookies are generally harmless, but these ones can track everything you do on the net and report it to advertisers or worse.
Hidden Dialers
These evil programs can cost you thousands of dollars by making you access the Internet via a premium-rate number instead of your regular provider.
Worms
The program prevents malicious software from distributing email in your name with viruses and other malware in attachments.
Key Loggers
How do you feel about programs that record and transmit every keystroke you make, with all your personal secrets and credit card details? Not nice? Not nice! So get rid of them!
Trojan Horses
A Trojan Horse or “Trojan” is a hidden program that doesn’t do any damage directly. But it enables hackers to control your computer over the Internet and do practically anything they want – activate your webcam, send spam, attack other computers, use your banking software…all in your name.
Sunday, November 23, 2008
Install xp os from pen drive
There may be sometimes problem with your CD/DVD drive,hence u may not able to reinstall your OS(XP) at the time of need.So here is a alternative way u can use your pen drive(USB flash drive) to boot from that and install XP from that instead of XP cd.So here is the way how u can make your pen drive as XP bootable and install from that..........Lipak
What do you need?
1. Windows Xp installation disk
2. Access to PC with working CD Cd-ROM DVD drive.
3. This file solution.rar .
then,
1. Download solution.rar file
2. Unpack solution.rar file on drive C, you should have a folder named C:\Dos
3. Put your pendrive ( at least 1GB) into working PC USB port
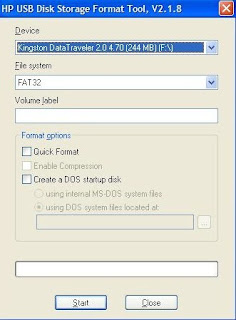
4. Go to the folder C:\Dos and run HpUSBformat.exe file - it should auto detect your pendrive disk, if not select form the list - set other options like on the image and click start. - now you have a pendrive with bootable dos on it.
5. Copy all other files from C:/Dos to your pendrive. ( you can overwrite existing ones) -
6. Put your Windows Xp installation disk into Cdrom and copy all files from CD to pendrive.
7. Boot your laptop with pendrive ( if you have problems, just check your BIOS or try to access boot menu )
8. Type sys d: and hit enter
9. Type format c:/q/s - accept and if it is formated go to step 11 - otherwise go to step 10
10. Type fdisk and hit enter -create new partition ( after restart boot with pendrive in) -go to step 9 and back here :) - type pqmagic and set your new partition active ( physical drive 2, Advanced A, ste Active - S, are you sure - Y, Exit - X )
11.Type nc and hit enter, and using Norton Commander, copy all files form pendrive to disk C: ( you can overwrite existing ones)
12. Restart Laptop without pendrive in it ( it should start from harddrive)
13. Type cd i386 and hit enter ( it will enter i386 folder)
14 Type winnt and hit enter
I am giving a link to download "Hp USB disk storage format tool".Click here
anyway u can get all the required tools from net
REMEMBER, DURING INSTALLATION - KEEP EXISTING FILE SYSTEM - DO NOT FORMAT, YOU CAN CONVERT IT TO NTFS LATER
Try this and enjoy...............Lipak
ReadyBoost-use flas drive(pen drive)as RAM in vista
Now most of us are using windows vista.It has many awesome features-one of them is "READY BOOST". Most of us even do not know about this feature.By this feature u can speed up your system by adding some virtual memory to your RAM(physical memory).So let's have a look about it - READY BOOST..............Lipak
Windows ReadyBoost can use storage space on some removable media devices, such as USB flash drives(such as PENDRIVE), to speed up your computer. When you insert a device with this capability, the AutoPlay dialog will offer you the option to speed up your system using Windows ReadyBoost.
If you select this option, you can then choose how much memory to use for this purpose. and this memory will be added as virtual physical memory(RAM).By this u will be able to speed up your system.
U can also open ReadyBoost option by right click on the flash drive in "my computer".Then go to properties.there u can go to ReadyBoost tab.allocate memory for that and and u will incrase your physical memory as long as pen drive is inserted in the computer.
U can feel this if u are running high end application like game or any multimedia work which requires more physical memory(RAM)But u will not be able to use those allocated memory any more untill u deallocate it.For ready boost u require atleast 235 MB free memory.
However, there are some situations where you may not be able to use all of the memory on your storage device to speed up your computer.Also it may depends upon the bad sectors and condition of the pendrive.So lets use and feel this highend feature to enhance the performance of your system...............Lipak
lipaknitjsr@gmail.com
Monday, November 10, 2008
UNIX Vs LINUX


UNIX:
Unix is a popular operating system.There are two "main" flavors, BSD, and System V. System V is what AT&T developed in 1969, nurtured and sold to people. BSD is the unix that came from Berkeley University.We people have generally interaction with System V unix.
It is a multi-processing, multi-user, family of operating systems that run on a variety of architechtures. UNIX allows more than one user to access a computer system at the same time.
It is the OS in which kernel interacts directly with the hardware.kernal is consider to be heart of this os.In this Operating system everything is considered as a file,provides greater security.
Ex: posix
LINUX:
Linux is an Operating system which use unix as its base and gives further more facilities and applications.Linux was first released by its inventor Linus Torvalds in 1991. Combining the Linux kernel with the GNU software forms the basis of the operating system family generally known as 'Linux'.
Merely speeking GUI is made in linux having unix as its core.Differnent organizations used the UNIX kernal and added their own essence to form their own version of linux.
Ex: Redhat, Fedora, Solaris,AIX,Ubuntu,Susee, Mandrake . .
Both UNIX and LINUX are Open source ...............Lipak
Wednesday, November 5, 2008
ANTIVIRUS - RANKING AND FACT


ACCORDING TO MY EXPERIENCE AND REVIEW OVER DIFFERENT PC MAGAZINES I CONCLUDE RANKING OF DIFFERENT ANTIVIRUS AS BELOW.NEVERTHELESS USE OF ANTIVIRUS DEPENDS UPON YOU,YOUR WORK AND USE OF PC.SOME ANTIVIRUS PROTECT YOUR PC WELL BUT IT SLOWS DOWN YOUR PC WHICH YOU MAY NOT LIKE.BUT IF U USE YOUR PC ROUGHLY AND USE INTERNET REGULARLY THEN IT NEEDS A GOOD ANTIVIRUS.SOME ANTIVIRUS ALSO BLOCK SOME USEFUL PROGRAMS WHICH U MAY NOT LIKE.LETS HAVE LOOK AT RANKING OF DIFFERENT ANTIVIRUS ............LIPAK
1.BITDEFENDER
2.McAfee VIRUS SCAN
3.KASPERSKY LAB KASPERSKY ANTI VIRUS PERSONAL
4.F-SECURE ANTIVIRSU
5.TREND MICRO
6.PANDA TITANIUM ANTIVIRUS AND ANTISPYWARE
7.ESET NODE 32
8.ANTIVIR PERSONAL ANTIVIRUS
9.NORTON SYMANTEC ANTIVIRUS
10.AVG ANTIVIRUS
CLICK HERE TO VIEW RANKING AND MORE
Subscribe to:
Comments (Atom)
